Openshift Security Guide
Openshift restricted codeready workspaces authenticate rep redhat Under the hood of cloud computing: openshift support services Openshift troubleshooting and operations
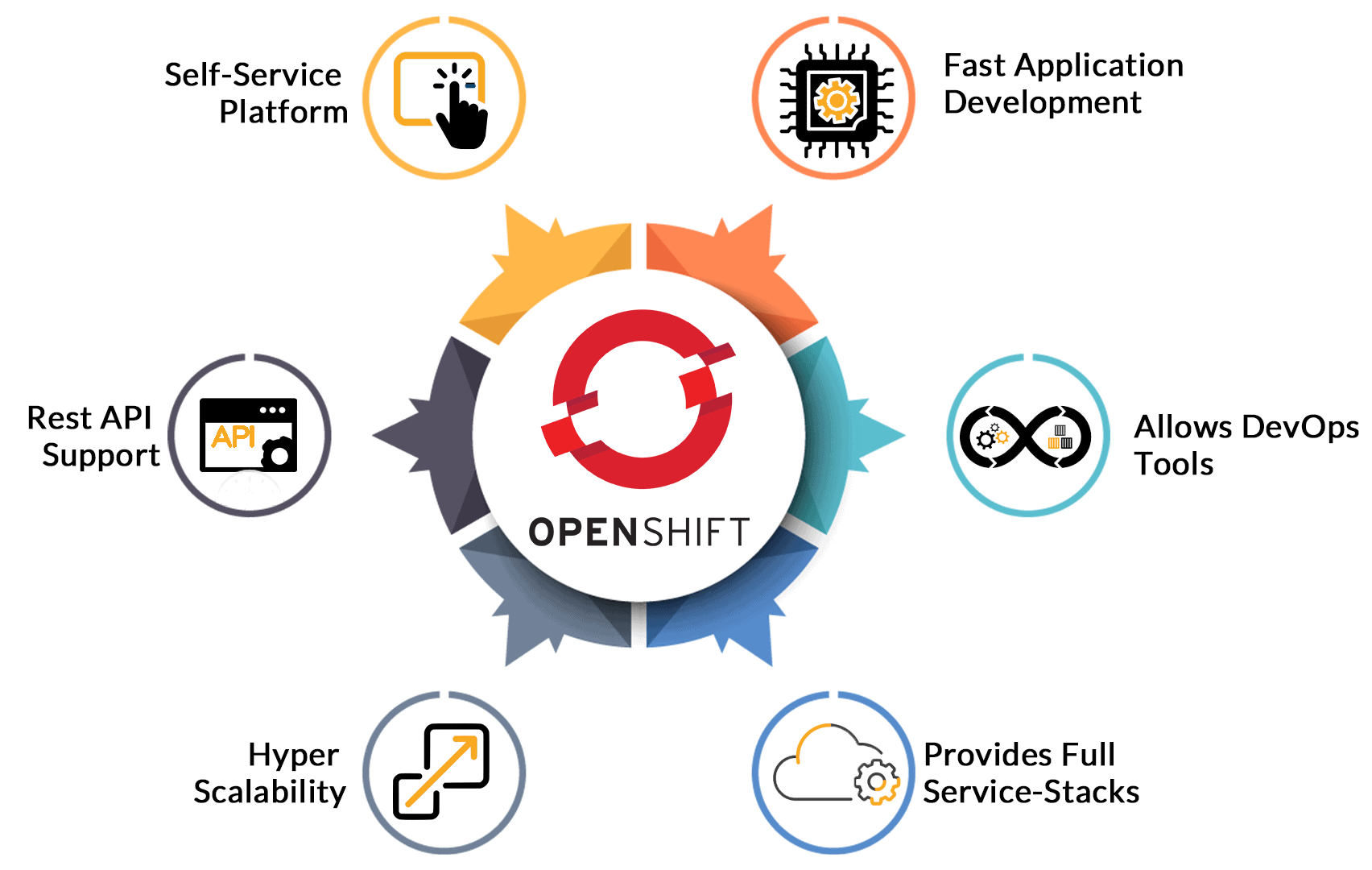
Openshift Interview Questions And Answers - GoLogica
Openshift operations namespace epg Openshift dye Security aspects with openshift
How to install codeready workspaces in a restricted openshift 4
Openshift security guide by red hatOpenshift writing What administrators should know about openshift?How to deploy openshift origin okd on fedora 29 server.
Why openshift? – shekhar gulatiOpenshift use cases How to install and deploy red hat openshift container platform 4.6 on5 red hat openshift benefits you may not have realized.

Dye your mind red: openshift in a diagram – spirited engineering
Easing security compliance with the openshift compliance operator: part 2Automated application packaging and distribution with openshift Openshift networking and network policies – techbloc.netOpenshift ibm cloud security automation started certificates diagram hat red domains renew automatically web tutorials tutorial.
Security practices in openshiftAdding security layers to your app on openshift — part 2 Jboss as7 security on openshiftOpenshift security guide: our first virtual book sprint experience.

How to use openshift service registry
Building modern ci/cd workflows for serverless applications with redInstalling a highly-available openshift origin cluster Compliance openshift operator easingOpenshift architecture installing ansible.
Security practices in openshiftOpenshift security best practices Securing cloud applications on openshift (sem) – sysdigOpenshift interview questions and answers.

Openshift security best practices
Red hat openshiftOpenshift online for public cloud application hosting Openshift security guide by red hatOpenshift gologica.
Openshift helm automated operators packagingOpenshift docs Openshift network networking pod egress policiesOpenshift: cos'è e perché piace ai dev, agli ops e al business.

Openshift security jboss as7
Openshift securingOpenshift serverless introduction hands Openshift messaging components cloud computing hood underOpenshift administrators virtualization.
Openshift serverless pipelines operators cd hat red installed ci workflows argo applications building modern part under figureOpenshift hat red service catalog Openshift booksprintsSecurity practices in openshift.

Openshift keycloak authentication authorization configured simplified backend
Openshift okd fedora deployHands on introduction to openshift serverless Chapter 6. deployment openshift container platform 3.9.
.